Two-factor authentication to the server via ssh
Initial Setup
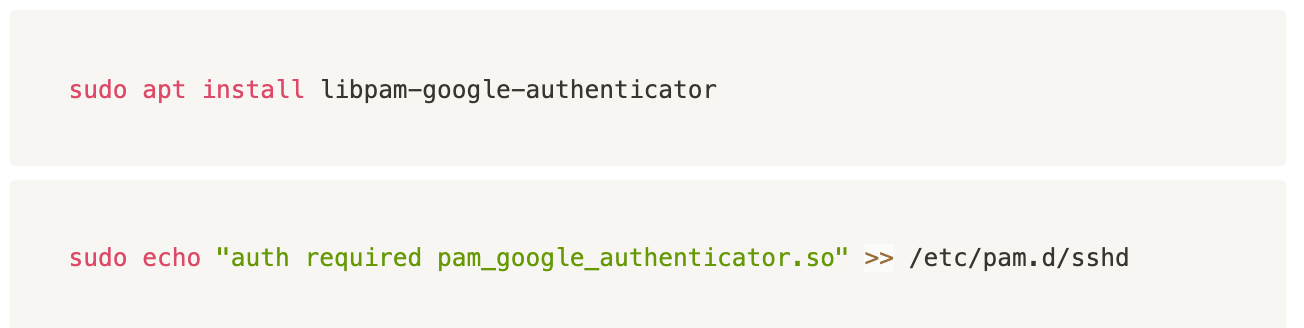
Setting up Google Authenticator

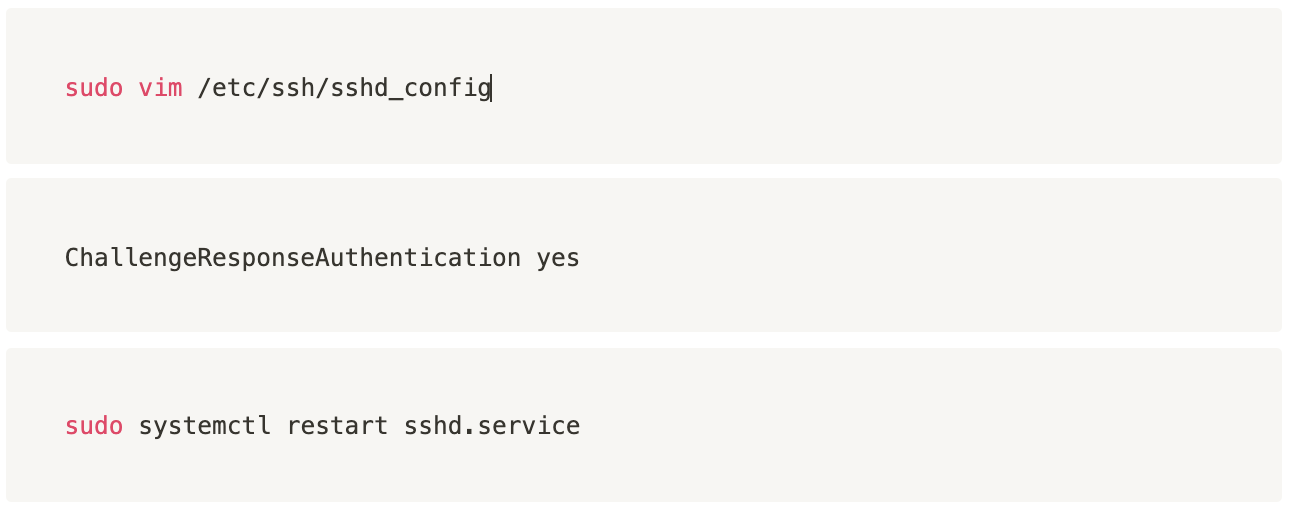
Enable mandatory verification of Google Authenticator on the server

Sources:
Last updated