Creating an L2TP vpn tunnel over IPSec
Setting up IPSec
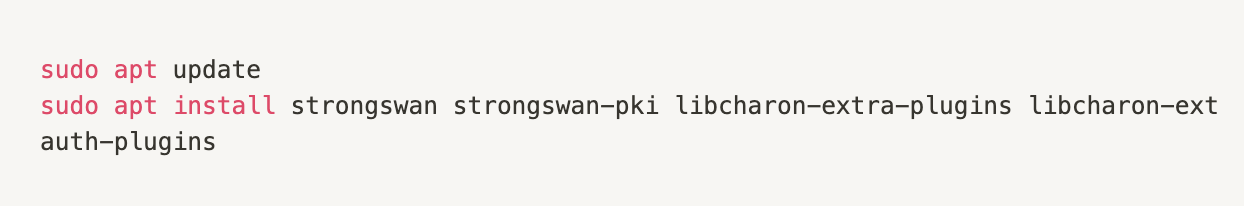

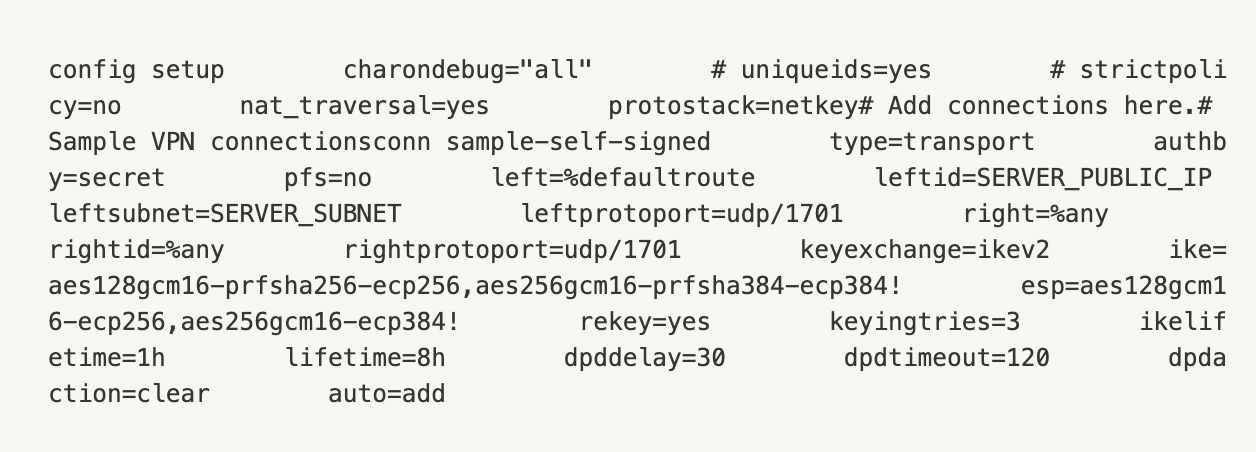


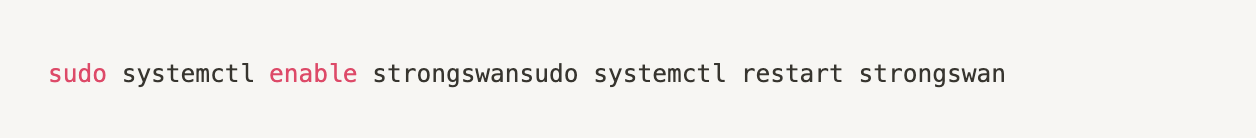
Setting up L2TP



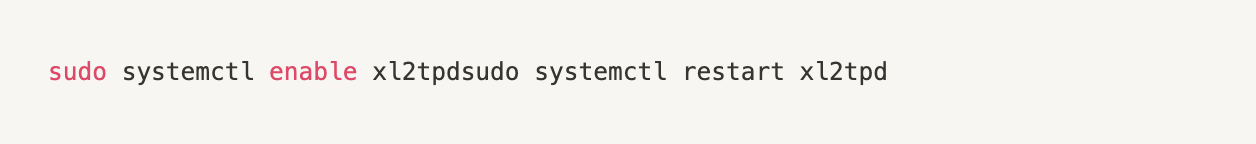
Setting up PPP





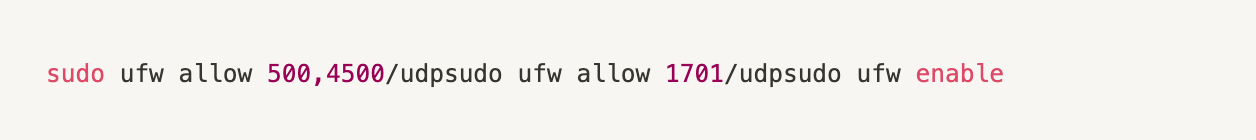
Adding firewall rules (does not work temporarily with the firewall)
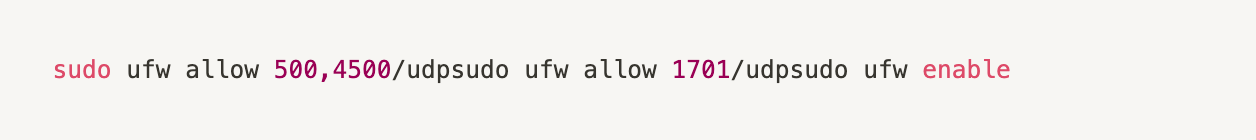
NAT settings
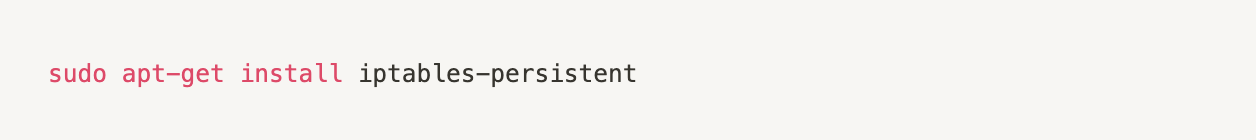
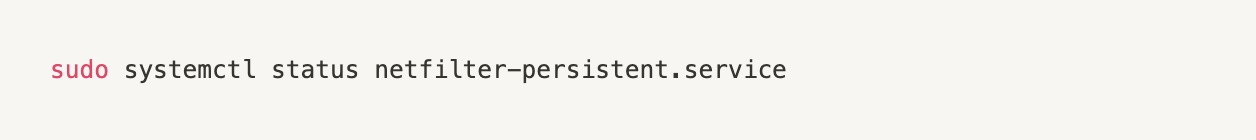

Sources:
Last updated